CVE Management & Reporting
If you've spent much time around code, you probably know that CVEs (common vulnerabilities and exposures) are a fact of life. As such, CVE management and mitigation is a key part of an organization's practices in AppSec and DevSecOps.
Through our support for common open-source CVE detection tools, MergeStat can be used as a purely open-source solution for reporting on CVEs detected across source code in an org.
It's important for organizations of any size to apply best practices in source code security, as the potential impact of not doing so could be catastrophic, as recent high profile security breaches frequently remind us.
MergeStat can be used to gain visibility into CVEs detected across all codebases in an organization (across multiple Git providers if necessary). This is valuable for:
- A point-in-time overview of an organization's security posture (with respect to CVE management)
- Driving initiatives to reduce
CRITICALandHIGHseverity CVEs across the org - Prioritizing efforts around AppSec and DevSecOps vulnerability mitigations
- Identifying which code bases (or teams) require more support or security investment
- Generally querying (asking ad-hoc questions) and reporting on the presence of known CVEs throughout an org, across teams and projects
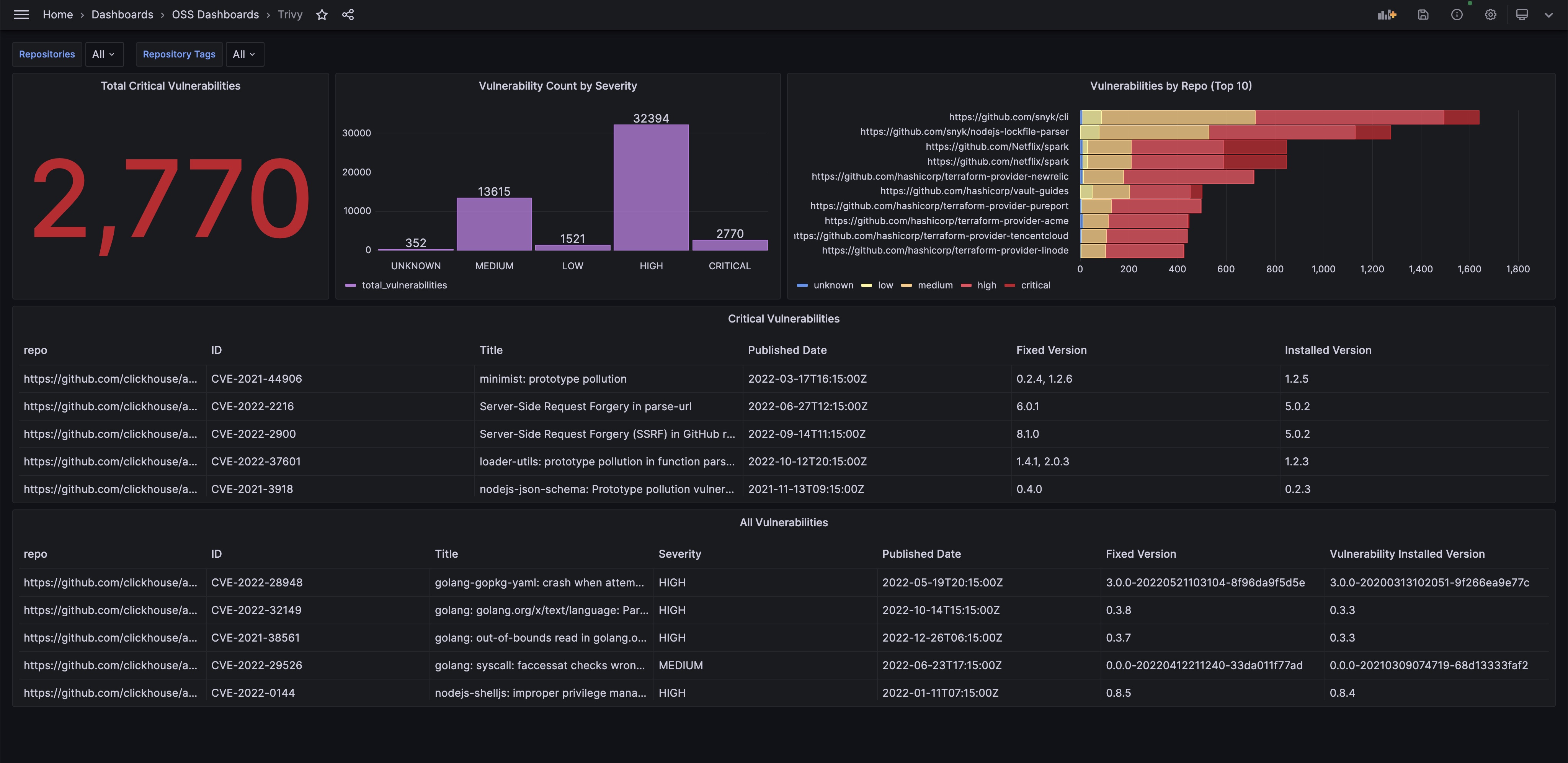 Screenshot of a MergeStat CVE dashboard in Grafana using data from the Trivy CVE scanner.
Screenshot of a MergeStat CVE dashboard in Grafana using data from the Trivy CVE scanner.
How does it work?
- MergeStat supports syncs that run Trivy and Grype (two open-source CVE scanners) on many Git repos (including across multiple hosts).
- MergeStat schedules these syncs, running them regularly and storing their output in a PostgreSQL database for reporting and ad-hoc querying.
- The detected CVE data may be queried with SQL in downstream reporting tools, or in the MergeStat application directly.
Setup
To get started, first you'll need a running instance of MergeStat. Check out our guide here on running an instance locally and adding your repos to begin.
Once your repos have been added, you'll wanted to enable two syncs.
One for Trivy:
and another for Grype:
Once these have been enabled on your repos, MergeStat will regularly run scans using these tools (on the default git branch) and stash the results in Postgres. You should now see the following tables & views begin to populate with data:
trivy_repo_scanstrivy_repo_vulnerabilitiesgrype_repo_scansgrype_repo_vulnerabilities
Queries & Examples
Now that we have data flowing for our repos from these two scanners, we can begin making use of it 🎉.
These examples will use the trivy_* tables.
Similar SQL can be composed for the grype_* tables as well.
CVE Overview
These queries offer a broad survy of CVEs detected across repos.
-- count which repos have the most CVEs (detected by Trivy)
-- regardless of severity
SELECT repo, count(*) FROM trivy_repo_vulnerabilities
JOIN repos ON trivy_repo_vulnerabilities.repo_id = repos.id
GROUP BY repo
ORDER BY count(*) DESC
-- count which repos have the most CVEs (detected by Trivy)
-- and group results by severity
SELECT repo, vulnerability_severity, count(*) FROM trivy_repo_vulnerabilities
JOIN repos ON trivy_repo_vulnerabilities.repo_id = repos.id
GROUP BY repo, vulnerability_severity
ORDER BY vulnerability_severity, count(*) DESC
-- count CVEs (detected by Trivy) by type
-- i.e. from Go modules vs NPM
SELECT type, count(*) FROM trivy_repo_vulnerabilities
GROUP BY type
ORDER BY count(*) DESC
-- count of trivy vulnerabilities by id
SELECT count(*) vulnerability_id, vulnerability_title, type FROM trivy_repo_vulnerabilities
GROUP BY vulnerability_id, vulnerability_title, type
ORDER BY count(*) DESC
Dashboard Starters
You can find a Trivy vulnerability management Grafana dashboard here. This can be imported directly into a Grafana instance.
// TODO We're putting together additional drop-in dashboards and examples for other data tools, check back soon for more.